Fixing Save as Adobe PDF Crashes
There have been many reported instances of the "Save as Adobe PDF" workflow crashing regardless of application, but precious few workarounds or resolutions. In troubleshooting, I discovered that there were three instances of the "Save as Adobe PDF.action" in three different locations: /Library/Automator; ~/Library/Automator; and /System/Library/Automator. By eliminating all except the version in /System/Library/Automator, the workflow started behaving, and I was able to cut PDFs directly from the Print dialog.
Submitted by
John Zielinski
Recent TidBITS Talk Discussions
- Alternatives to MobileMe for syncing calendars between iPad/Mac (1 message)
- Free anti-virus for the Mac (20 messages)
- iTunes 10 syncing iPod Touch 4.1 (2 messages)
- Thoughts about Ping (16 messages)
Published in TidBITS 1016.
Subscribe to our weekly email edition.
- Aperture 3.0.1 Update Addresses Stability Problems
- Mac Enterprise Numbers Expected to Increase in 2010
- YouTube Halts Full Support for Older Browsers on 13 March 2010
- Prevent Apple Mail from Auto-Completing the Wrong Address
- Does the iPhone OS Need Multitasking?
- TidBITS Watchlist: Notable Software Updates for 1 March 2010
- ExtraBITS for 1 March 2010
Clipperz Does the Impossible: A Safe Online Password Manager
For safety's sake, I use a different, randomly generated password for every Web form I encounter. Since I don't know any of these passwords, I store them, password-protected, using a password keeper application. But this technique, although it's pretty secure (unless someone sneaks into my house and bonks me over the head while the password keeper is open), works only if I'm sitting at my own computer. How can I access these passwords safely and securely from any computer?
Enter Clipperz.
I first heard about Clipperz on an IT Conversations podcast, and my immediate reaction was, "Why didn't anyone tell me about this sooner?" Clipperz is a Web application, so you navigate to it in a browser; thus, you have access to your online passwords exactly when you need them, namely, whenever you're online. When you arrive at the clipperz.com Web site, you enter your username and a master passphrase; the guessability of this combination is the weakest link in the chain, of course, so you should use a rather long and unnatural passphrase. However, the passphrase itself is not sent to clipperz.com during login. In fact, clipperz.com doesn't know your username, your master passphrase, or any of your passwords!
How can this be? Well, clipperz.com is what's called a "zero-knowledge database." It doesn't store anything in cleartext; everything is encrypted, and clipperz.com doesn't have the key. All of the stored data is encrypted; communication with Clipperz is also encrypted (doubly so, since it also is transmitted using SSL). All the encryption and decryption happens at your end - in the browser. This is possible because of the speed of modern computers and JavaScript implementations (JavaScript data is lost when you change Web pages, so Clipperz uses AJAX to refresh screens while keeping you on the same page). Moreover, the apparent weakest link, the initial password-based authentication, uses Secure Remote Password (SRP) authentication, which is itself zero-knowledge (clipperz.com knows only a public key derived from your username and passphrase), and is as secure as password-based authentication can possibly be - probably vastly more secure than any other password-based authentication you ever do on the Internet. Finally, all of Clipperz's code is open source - since, as you doubtless know, security by secrecy is the worst security of all.
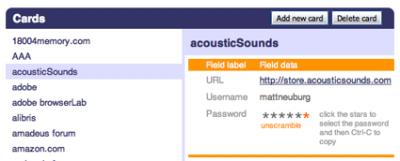
The screenshot shows the simple interface that you see once you're logged in. It's a straightforward "rolodex" of information. Down the left side run the names of your "cards"; click the name of a card and you're shown its "fields." I'm not afraid to show you this because the password field is always portrayed as six stars, which you can copy (using Command-C, not Control-C as stated in the screenshot) to paste into the password field of a Web form, which is presumably open in another window. (If you're on a public machine, remember to copy something else onto the clipboard later, so as not to leave your password there in cleartext.) You can also "unscramble" the password, showing it directly in cleartext; this is safe as long as no enemy spies are sitting behind you.
Naturally, online passwords are not the only data you might store securely this way. You could keep credit card numbers or anything else you might need while online. A card's fields are customizable, so you can set up a card to display whatever might be appropriate for a particular datum.
Another cute feature is that you can set up "one-time passwords." These are login passphrases for clipperz.com that are deleted as soon as they are used. As every reader of spy novels knows, a one-time pad is the most secure form of encryption. So if you're in a public space, use one of your one-time passwords; even if a spy sitting behind you can memorize your finger movements on the keyboard, that knowledge will be useless.
And here's the icing on the cake. I've said that the encryption and decryption happens in the browser; I've also said that the data stored at clipperz.com is encrypted. Hence, there is no loss of security if you store the data from clipperz.com on your machine. And that is just what Clipperz allows you to do. You can download a (very large) Web page containing the encrypted data and all the JavaScript. When you open that Web page with your browser, it's exactly like talking to clipperz.com - you still have to log in with your username and passphrase - but you're not talking to clipperz.com; you're working offline. So this one downloaded Web page is doing for me everything that my password keeper application was doing previously! The only thing missing is editability; you're working with a read-only copy of your data. Pretty slick, eh?
Clipperz isn't perfect. Copying the scrambled password doesn't work reliably - but the Clipperz folks are working on a new Web interface, currently called the "gamma," which solves that problem. The interface for some operations, such as entering multiple cards by importing from a text file, is highly confusing (I succeeded, but only after much experimentation). The overall interface is, alas, clumsy on an iPhone; there is a mobile version of the Web interface, but it doesn't work for me at all. Finally, there's a promising feature called "direct login" that lets you click a link and automatically, with no further action on your part, go to the target Web site's login page, enter your username and password, and submit the form; but it doesn't work for all Web sites, and the interface for editing a direct login is somewhere between clumsy and non-existent (though this, too, is nicely solved in the new "gamma" interface).
Quibbles aside, I've found Clipperz a tremendous help in my daily Web life. It lets you access your online passwords, online, regardless of what computer you're using. It's free, it's open source, it's safe and secure, it's ingenious, and it's way cool. What more could you ask? Perhaps you'll give it a try, and you, too, will be wondering why no one told you about this sooner.
Typed notes are blended with recorded audio, video, and slides
to create notes that make more sense when you need them most.
Learn more at <http://www.usefulfruit.com/tb>!
Lastpass is also host-proof-hosting based (client side encrypt). Plus supports some very nice multifactor authentication methods including yubikey.
And if you're in a shared password situation (i.e. server management) lastpass has some nice facilities for that, as well as device management (e.g. demand multifactor from desktop, lock iPhone login to single device ID).
And there is no 'reverse engineering' the code is completely open source.
I don't know if there's a neat solution that avoids displaying the password in clear text - maybe allowing copy/paste in several chunks in random order (e.g. copy chunk 1 and paste it, then copy chunk 2 and paste it before chunk 1, then copy chunk 3 and paste it at the end, etc)
LastPass lets you customize your preferences by computer: at your home desktop, you may want to stay logged-on as long as the browser is open; on a laptop, you may want to automatically log-off after a couple minutes of keyboard inactivity.
LastPass also has a well thought-out form-filling function, for completing addresses, account numbers, and so on.
One shortcoming of the web-based programs, however, is that they can only log-in via the browser; you can't automatically supply the password to an encrypted local file or folder, for example.