


 6.8 Description of the
Example Domain
6.8 Description of the
Example Domain


 6.8 Description of the
Example Domain
6.8 Description of the
Example Domain
First, we must install a new backup domain controller (BDC) with OS/2 Warp Server for e-business. The installation itself is straightforward because the BDC (\\DC02) has no network resources defined.
If network resources had been defined on this server, then migration of these resources would also be necessary. With this alternative scenario comes greater complexity.
The following shows the steps needed to install the new backup domain controller.
Install OS/2 Warp Server for e-business on the new system hardware. The
installation can be either a CD-ROM panel-driven attended installation or a
CID-based unattended installation. Make sure that the new system is configured
exactly the same as the original BDC, as it will later replace it (in this
case, \\DC02). The new BDC server must be installed with the role set to
BACKUP.
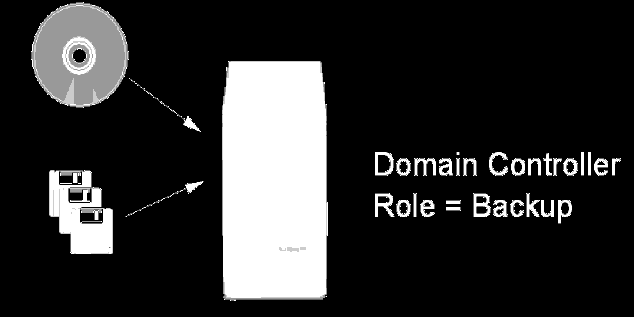
Figure 107: Installing the Backup Domain Controller
If the server is installed on the production network, do not allow any LAN Server services to start after installation.
This can be achieved by commenting out the NET START SRV statement in the STARTUP.CMD (add the letters REM and one space character before the aforementioned statement), or renaming STARTUP.CMD to another name. Or, you can rename the STARTUP.CMD file so it does not execute upon system startup.
For example:
REN STARTUP.CMD STARTUP.OLD
then press Enter.
Alternatively, the server can be installed on an isolated LAN segment. Make sure that the STARTUP.CMD file is renamed or changed as above prior to moving the system to the production LAN.
First, remove the existing BDC (\\DC02) from the network. This can be done in one of two ways. Either stop all of the LAN Server services or shut the system down completely.
You can stop the server by issuing the following command and following the prompts to stop the services:
NET STOP REQ /Y
then press Enter.
When the original BDC (\\DC02) has been removed from the network, the
newly-installed BDC (also configured as \\DC02) can be attached to the network
and started.
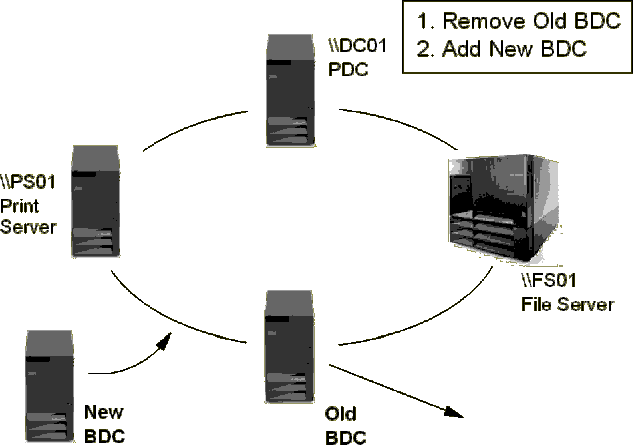
Figure 108: Attaching the Backup Domain Controller to the
Network
If the system is already attached to the network, simply start the server by issuing the following command:
NET START SRV
then press Enter.
Now the freshly installed OS/2 Warp Server for e-business image of the BDC (\\DC02) has replaced the original BDC (\\DC02). The PDC (\\DC01) is currently unchanged and will, therefore, continue to handle any logon requests. Up until this point, it is unlikely that any users will have experienced any disruption to service.
With the new BDC (\\DC02) in place, the LAN Server DCDB (Domain Control
Database) Replicator Service will start to replicate user and group information
from the PDC to the BDC (the \IBMLAN\DCDB subdirectory tree). This
enables the BDC to handle user logon requests whenever the domain controller is
busy.
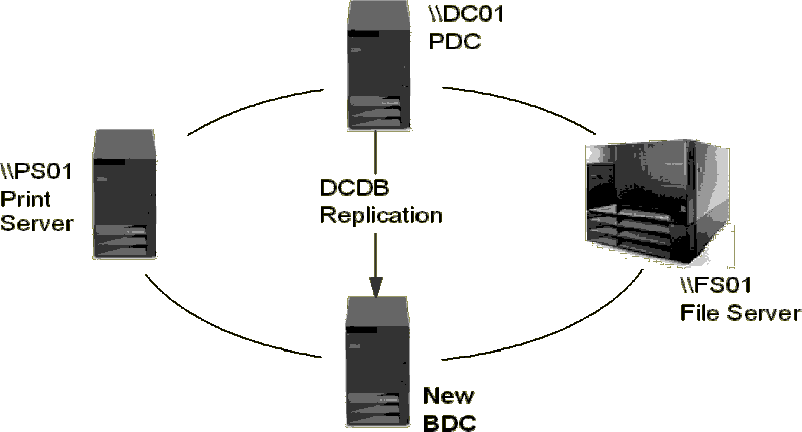
Figure 109: Domain Control Database (DCDB) Replication
Since server \\DC02 is already defined as a valid Machine ID as part of the group SERVERS as a server in the domain, no further action is needed.
Provided that the DCDBREPL service is started on both the PDC (\\DC01) and the BDC (\\DC02), then DCDB replication will start. The status of the replication can be verified by issuing the following command locally:
NET START
then press Enter
or by using the NET ADMIN command and issuing the following command (Note: that if expected results are not seen, both PDC and BDCs should be checked):
NET ADMIN \\DC01 /C NET START
then press Enter.
If the DCDBREPL service has started successfully, it will be displayed as
follows:
These services are started: REQUESTER MESSENGER SERVER NETLOGON LSSERVER DCDBREPL The command completed successfully. |
If the DCDBREPL service is not yet started, you must start it. You can do so by issuing the following command locally or by pre-pending the NET ADMIN syntax as above when issued from a remote system:
NET START DCDBREPL
then press Enter.
Occasionally, the DCDB replicator service will not function correctly. The problem is usually seen on the BDC with it not receiving a copy of the master user accounts database. If this happens, the problem must be resolved before continuing. Please refer to Section 6.9.4 Correcting DCDB Replication Problems if you find that there are problems. There are several procedures that can help you.
If DCDB replication is not working properly, it could be due to one of the following reasons:
The resolution for each of these situations is slightly different. In this section, the resolutions are described in turn.
The DCDBREPL Service uses a UserID on the BDC that effectively logs on to the PDC in order to receive the updates to the master accounts database. This is specified normally in the IBMLAN.INI file with the keywords:
Logon = Password =
If no user is logged on to the BDC, this can cause problems with the DCDB replication service.
To overcome this problem, you can set up a userid if one has not already been set up. You can do this by adding the information about userid and the password to the IBMLAN.INI of the BDC and then adding a userid. In our example, you could do this logged on to a server in the domain as an administrator as follows:
NET ADMIN \\DC01 /C NET USER DCDBUSR /PASSWORDREQ:NO /PRIV:ADMIN /WORKSTATION:DC02
then press Enter.
The /WORKSTATION parameter makes sure that this user only has access when logged on at DC02.
If the user defined lacks access rights, grant them. Otherwise, the replication will fail.
If a backup domain controller should fail while starting the server part with a NET3062 error, it is usually for one of two reasons.
We will now describe the scenarios in more detail.
Using the name convention already discussed, the PDC is \\DC01, and the BDC is \\DC02. In order to solve these problems, you must log on as administrator and complete the following steps. On the BDC, type the command:
NET START SRV
then press Enter.
The following result is displayed:
The SERVER service is starting.... The SERVER service could not be started. NET3062: The sub-service NETLOGON failed to start. For more information, type HELP NET3062.
To find out what the problem is, we have to look into the error log of the machine by typing the following command on server \\DC02:
NET ERROR
then press Enter.
The following output is displayed:
Program Message Time NETLOGON 3055 10-22-96 03:33pm An error occurred. Refer to the help for the following message: NET3084: The user accounts system is not configured correctly. 0C 0C .. SERVER 3113 10-22-96 03:33pm NET3113: Initialization failed because the requested NETLOGON service could not be started. The command completed successfully.
This means that this new server is not defined into the domain controller data base (DCDB). In order to solve this problem, we have to do the following steps. First, you need to log on as an administrator to the domain by typing the following command (which is not needed if you have already logged on):
LOGON ADMIN /P:PASSWORD /V:D
where ADMIN and PASSWORD are valid variables. Then you should add the backup domain controller to the database by typing the following commands at the keyboard of the primary domain controller:
NET ADMIN \\DC01 /C NET USER DC02 /PASSWORDREQ:NO /USERCOMMENT:"Backup DC" /ADD
After that, issue the following command:
NET ADMIN \\DC01 /C NET GROUP SERVERS DC02 /ADD
Finally, log off and start the server with the following commands:
LOGOFF NET START SRV
The following result should be displayed:
The SERVER service is starting.... The SERVER service was started successfully.
The second scenario can also be solved. On server \\DC02, type the following command:
NET START SRV
The following result is displayed:
The SERVER service is starting.... The SERVER service could not be started. NET3062: The sub-service NETLOGON failed to start. For more information, type HELP NET3062.
In order to find out the cause of the problem, we have to look into the error log of the machine by typing the following command:
NET ERROR
The following result is displayed:
Program Message Time NETLOGON 3210 10-22-96 03:59pm NET3210: This server failed to authenticate with DC1, the domain controller for domain WSDOMAIN. 05 00 .. NETLOGON 3056 10-22-96 03:59pm NET3056: A system error has occurred. 05 00 .. SERVER 3113 10-22-96 03:59pm NET3113: Initialization failed because the requested NETLOGON service could not be started. The command completed successfully.
The following process will resolve the problem. Copy these two files onto a diskette:
Go back to the console of \\DC02. Copy the two files from the diskette to the server and set the server role into standalone. Log on locally. Type the following commands:
COPY A:\PWDEXP.EXE X:\IBMLAN\NETPROG
where X: is the drive letter where you installed OS/2 LAN or Warp Server. Then issue the following commands:
NET ACCOUNTS /ROLE:STANDALONE LOGON USERID /P:PASSWORD /V:L
If this the first attempt of the server to reach the PDC, the default user ID will be USERID and the default password will be PASSWORD. Otherwise, ADMIN and PASSWORD will be valid variables (already) defined in your local database file, NET.ACC.
Extract the (encrypted) password from \\DC02 by typing the following command:
PWDEXP DC02
For example, a result like this could be displayed:
DC2:AAD3B435B51404EEAAD3B435B51404EE
Do it again and write the result to a file on diskette by typing the following command:
PWDEXP DC02 > A:\DC02.PWD
Log off from the local database of \\DC02 and perform a logon to the PDC \\DC01 by typing the following commands:
LOGOFF LOGON ADMIN /P:PASSWORD /V:D
where ADMIN and PASSWORD are valid variables.
Get the saved file from the diskette and copy it to the PDC by typing the following command:
COPY A:\PWDIMP.EXE \\DC01\IBMLAN$\NETPROG
and type the following command to display the file:
TYPE A:DC02.PWD
For example, the result could be:
DC02:AAD3B435B51404EEAAD3B435B51404EE
Continue typing the following command:
NET ADMIN \\DC01 /C PWDIMP DC02:AAD3B435B51404EEAAD3B435B51404EE
It is better to use the clipboard function in order to copy the data. If you make a mistake in the number/letter combination, you will not be able to log on.
Change the server role to Member or Backup of your domain by typing the following commands:
NET ACCOUNTS /ROLE:BACKUP LOGON USERID /P:PASSWORD /V:L
| Note |
|---|
|
For an additional server, you would need to change the first line to |
Finally, log off and start the server with the following command:
LOGOFF NET START SRV
The following result should be displayed:
The SERVER service is starting.... The SERVER service was started successfully.
Because there is a lot of room for error, and the process is tedious, we wrote a tool that basically performs the same function as has just been described. It is called RESYNCPW.EXE. We have included this tool on the CD-ROM accompanying this redbook.
When the DCDBREPL services have started successfully on both the PDC and the BDC, and when DCDB replication appears to be functioning correctly, we must verify that all data has been replicated. We do this in the following manner.
If the DCDB replication service is replicating correctly, a file called
OK.RP$ can be found in each of the \IBMLAN\DCDB subdirectories. To
check whether this is the case, issue the following command and press
Enter to display output that should look like the following:
[D:>]DIR \\DC02\IBMLAN$\DCDB\*.RP$ /S /B \\DC02\IBMLAN$\DCDB\APPS\OK.RP$ \\DC02\IBMLAN$\DCDB\Data\OK.RP$ \\DC02\IBMLAN$\DCDB\DEVICES\OK.RP$ \\DC02\IBMLAN$\DCDB\FILES\OK.RP$ \\DC02\IBMLAN$\DCDB\IMAGES\OK.RP$ \\DC02\IBMLAN$\DCDB\LISTS\OK.RP$ \\DC02\IBMLAN$\DCDB\PRINTERS\OK.RP$ The command completed successfully |
If the output displays any files called NO_SYNC.RP$, this means that the servers are communicating with each other, but that the DCDB replication service updates may not be current, for example, if additional time is needed to complete the replication.
Initially, this does not represent a problem. However, if OK.RP$ is still not displayed after some time, of course dependent on network traffic and the replication parameters in the IBMLAN.INI file, then the problem must be resolved.
If the output displays any files called NO_MASTER.RP$, then there is already a problem. The PDC and BDC are not communicating with one another for one of the following reasons.
This situation must be corrected before progressing.
Please refer to Section 6.9.4.1 DCDBREPL Problem 1: User Not Logged On through Section 6.9.4.3 DCDBREPL Problem 3: NET3062 Errors, or refer to the on-line documentation for further information on how to correct this condition.
When the file OK.RP$ exists in the DCDB subdirectories, this is still not a total guarantee that replication has completed. This simply means that the PDC and the BDC are communicating, and that the DCDB replicator service is functioning.
In a large domain, the replication process can take a long time to complete. This is, of course, dependent on network traffic, the size of the domain, and IBMLAN.INI replication parameters.
We wrote a procedure called LSC.CMD (LAN Server Check and Statistics) to help make sure that the DCDB replication has completed successfully. We have included this tool on the CD ROM accompanying this Red Book. LSC was written to query information about the DCDB directories and to check the status of the server services. This is important because the NETLOGON and DCDBREPL services must be running for DCDBREPL to work properly.
The syntax of LSC.CMD is
LSC {*} {ServerName} {/STAT}
where:
Figure 112 through Figure 114
illustrates the use of the utility. Key outputs are highlighted in bold.
* LSC Version 2.34 * Server Name: \\DC01 *------------------------------------------------- * Get Accounts: *------------------------------------------------- Server Role: Primary server in the domain Domain controller for requester domain: \\DC01 *------------------------------------------------- * Get Users: *------------------------------------------------- Number of users defined on \\DC01 : 60 *------------------------------------------------- * Get services: *------------------------------------------------- REQUESTER MESSENGER SERVER NETLOGON LSSERVER DCDBREPL *------------------------------------------------- * Check DCDB Replicator: *------------------------------------------------- DCDB replicator running Checking DCDB tree: 1 APPS * -none- 2 DEVICES * -none- |
|
The following figure displays the output of \\DC02, a backup domain
controller.
|
The syntax of LSDCDB.CMD is
LSCDCDB {DCName} {/FIX}
| Note |
|---|
|
Only run LSDCDB /FIX on the Primary Domain Controller. Changes made on the PDC are replicated to the BDC. Therefore, it does not make sense to fix the BDC since errors that existed on the PDC will continue to be replicated during normal server operation re-introducing a problem. |
Figure 115 and Figure 116
illustrate the output of LSDCDB.
* LSDCDB Version 3.09 * Server Name: \\DC01 * Role: Primary server in the domain * Getting all users from: \\DC01 * Total users: 60 * Getting SysFileTree from: \\DC01\ibmlan$\users * Total directories: 36 ( 1/36) \\DC01\ibmlan$\dcdb\users\$SRV174 ( 2/36) \\DC01\ibmlan$\dcdb\users\ALAINADM ( 3/36) \\DC01\ibmlan$\dcdb\users\CID ( 4/36) \\DC01\ibmlan$\dcdb\users\CID01 ( 5/36) \\DC01\ibmlan$\dcdb\users\FRANKADM ( 6/36) \\DC01\ibmlan$\dcdb\users\JPADM ( 7/36) \\DC01\ibmlan$\dcdb\users\MAT ( 8/36) \\DC01\ibmlan$\dcdb\users\USER001 ( 9/36) \\DC01\ibmlan$\dcdb\users\USER002 (10/36) \\DC01\ibmlan$\dcdb\users\USER003 (11/36) \\DC01\ibmlan$\dcdb\users\USER004 (12/36) \\DC01\ibmlan$\dcdb\users\USER005 (13/36) \\DC01\ibmlan$\dcdb\users\USER006 (14/36) \\DC01\ibmlan$\dcdb\users\USER007 (15/36) \\DC01\ibmlan$\dcdb\users\USER008 (16/36) \\DC01\ibmlan$\dcdb\users\USER009 (17/36) \\DC01\ibmlan$\dcdb\users\USER011 (18/36) \\DC01\ibmlan$\dcdb\users\USER012 |
(19/36) \\DC01\ibmlan$\dcdb\users\USER013 (20/36) \\DC01\ibmlan$\dcdb\users\USER014 (21/36) \\DC01\ibmlan$\dcdb\users\USER015 (22/36) \\DC01\ibmlan$\dcdb\users\USER016 (23/36) \\DC01\ibmlan$\dcdb\users\USER017 (24/36) \\DC01\ibmlan$\dcdb\users\USER018 (25/36) \\DC01\ibmlan$\dcdb\users\USER019 (26/36) \\DC01\ibmlan$\dcdb\users\USER020 (27/36) \\DC01\ibmlan$\dcdb\users\USER021 (28/36) \\DC01\ibmlan$\dcdb\users\USER022 (29/36) \\DC01\ibmlan$\dcdb\users\USER023 (30/36) \\DC01\ibmlan$\dcdb\users\USER024 (31/36) \\DC01\ibmlan$\dcdb\users\USER025 (32/36) \\DC01\ibmlan$\dcdb\users\USER026 (33/36) \\DC01\ibmlan$\dcdb\users\USER027 (34/36) \\DC01\ibmlan$\dcdb\users\USER028 (35/36) \\DC01\ibmlan$\dcdb\users\USER029 (36/36) \\DC01\ibmlan$\dcdb\users\USER030 |
Figure 117 represents the output of the Backup Domain
Controller in the process of DCDB replication.
* LSDCDB Version 3.09 * Server Name: \\DC02 * Role: Backup server in the domain * Getting all users from: \\DC02 * Total users: 60 * Getting SysFileTree from: \\DC02\ibmlan$\users * Total directories: 13 ( 1/13) \\DC02\ibmlan$\dcdb\users\$SRV174 ( 2/13) \\DC02\ibmlan$\dcdb\users\ALAINADM ( 3/13) \\DC02\ibmlan$\dcdb\users\CID ( 4/13) \\DC02\ibmlan$\dcdb\users\CID01 ( 5/13) \\DC02\ibmlan$\dcdb\users\FRANKADM ( 6/13) \\DC02\ibmlan$\dcdb\users\JPADM ( 7/13) \\DC02\ibmlan$\dcdb\users\MAT ( 8/13) \\DC02\ibmlan$\dcdb\users\USER001 ( 9/13) \\DC02\ibmlan$\dcdb\users\USER002 (10/13) \\DC02\ibmlan$\dcdb\users\USER003 (11/13) \\DC02\ibmlan$\dcdb\users\USER004 (12/13) \\DC02\ibmlan$\dcdb\users\USER005 (13/13) \\DC02\ibmlan$\dcdb\users\USER006 |
Figure 118 shows the actual problems (highlighted in
bold for clarity).
|
(31/35) \\DC01\ibmlan$\dcdb\users\USER026 (32/35) \\DC01\ibmlan$\dcdb\users\USER027 (33/35) \\DC01\ibmlan$\dcdb\users\USER028 (34/35) \\DC01\ibmlan$\dcdb\users\USER029 (35/35) \\DC01\ibmlan$\dcdb\users\USER030 |
After running the procedure with the /FIX parameter, a look in the
log file lists the changes that were made, as shown in
Figure 120.
03/12/98 21:16:57 Del ACL on \\DC01\ibmlan$\dcdb\users\CID 0 03/12/98 21:16:57 Adding ACL on: \\DC01\ibmlan$\dcdb\users\CID CID:RWCXDAP 03/12/98 21:16:57 Set ACL on \\DC01\ibmlan$\dcdb\users\CID CID:RWCXDAP 03/12/98 21:16:57 Del ACL on \\DC01\ibmlan$\dcdb\users\CID\BATCH 0 03/12/98 21:16:57 Adding ACL on: \\DC01\ibmlan$\dcdb\users\CID\BATCH CID:RWCXDAP 03/12/98 21:16:57 Set ACL on \\DC01\ibmlan$\dcdb\users\CID\BATCH CID:RWCXDAP 03/12/98 21:16:57 Del ACL on \\DC01\ibmlan$\dcdb\users\USER005 0 03/12/98 21:16:57 Adding ACL on: \\DC01\ibmlan$\dcdb\users\USER005 USER005:RWCXDAP 03/12/98 21:16:57 Set ACL on \\DC01\ibmlan$\dcdb\users\USER005 USER005:RWCXDAP 03/12/98 21:16:57 Del ACL on \\DC01\ibmlan$\dcdb\users\USER005\BATCH 0 03/12/98 21:16:57 Adding ACL on: \\DC01\ibmlan$\dcdb\users\USER005\BATCH USER005:RWCXDAP 03/12/98 21:16:57 Set ACL on \\DC01\ibmlan$\dcdb\users\USER005\BATCH USER005:RWCXDAP 03/12/98 21:16:57 Del ACL on \\DC01\ibmlan$\dcdb\users\USER010 2222 Could not delete Access profile 03/12/98 21:16:57 Adding ACL on: \\DC01\ibmlan$\dcdb\users\USER010 USER010:RWCXDAP 03/12/98 21:16:57 Set ACL on \\DC01\ibmlan$\dcdb\users\USER010 USER010:RWCXDAP 03/12/98 21:16:57 Del ACL on \\DC01\ibmlan$\dcdb\users\USER010\BATCH 0 03/12/98 21:16:57 Adding ACL on: \\DC01\ibmlan$\dcdb\users\USER010\BATCH USER010:RWCXDAP 03/12/98 21:16:57 Set ACL on \\DC01\ibmlan$\dcdb\users\USER010\BATCH USER010:RWCXDAP |
If changes are necessary to correct problems with the PDC, it is advisable to make them before proceeding to the next step. Repeat the appropriate procedures described in Section 6.9.3 Allowing DCDB Replication to Complete and then to wait for a reasonable period of time for the replication to complete successfully.
When you are confident that the DCDB and access controls are OK, continue to the next step.