Managing program components
For each program on your computer, you can specify whether Zone Labs security software will authenticate the base executable only, or the executable and the components it loads. In addition, you can allow or deny access to individual program components.
The Components List contains a list of program components for allowed programs that have tried to access the Internet or the local network. The Access column indicates whether the component is always allowed access, or whether Zone Labs security software should alert you when that component requests access.
The Components List is organized in alphabetical order. You can sort the components in the list by any column by clicking on the Component column header. As you use your computer, Zone Labs security software detects the components that are used by your programs and adds them to the Components List.
To access the Components List:
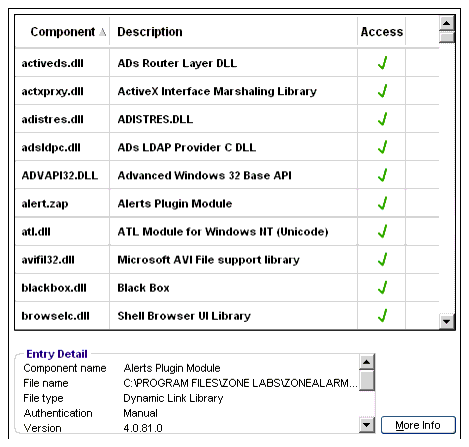
To grant access permission to a program component: