 Security
tab
Security
tab  Security
tab
Security
tab
|
Click the numbers to learn about specific controls, or read an introduction. To reach this tab: 1. Go to Program Control /Programs tab |
Use this tab to choose the type of authentication to be used for this program, and to set Advanced Program Control and filter options for this program.
Advanced Program Control tightens your security by preventing unknown programs from using trusted programs to access the Internet.
This is an advanced security feature intended to prevent malicious programs from hijacking trusted programs. However, some legitimate programs use indirect access. By default, the most common of these programs are given permission to access the Internet through other programs. without informing you.
To enable a program to use another program to access the Internet, select the check box labeled This program may use other programs to access the network.
![]() Note
By default, the following applications are allowed to use indirect access:
Note
By default, the following applications are allowed to use indirect access:
Use this area to enable or disable Web Filtering and Privacy protection for the selected program.
|
Option |
If selected |
|
Authenticate programs and components |
Whenever the program accesses the Internet or your local network, ZoneAlarm Pro uses the MD5 signature to verify that it is authentic and untampered with. If the program has loaded any components, ZoneAlarm Pro authenticates them as well. |
|
Authenticate program only |
ZoneAlarm Pro authenticates the program, but allows the program to load components without authenticating them. |
|
Use program file path only |
Instead of checking the MD5 signature, ZoneAlarm Pro will only check to see that the location of the program on your computer hasn't changed. This is a low-security option, but may be useful for programs that are frequently updated. |
![]() Tip
Zone Labs suggests using the Authenticate program only option the first
two times you use an application with ZoneAlarm Pro. This enables ZoneAlarm
Pro to "fingerprint" the programs components silently. After using
the application twice, select Authenticate programs and components, so
that ZoneAlarm Pro will check all components against their fingerprints when
a program accesses the Internet.
Tip
Zone Labs suggests using the Authenticate program only option the first
two times you use an application with ZoneAlarm Pro. This enables ZoneAlarm
Pro to "fingerprint" the programs components silently. After using
the application twice, select Authenticate programs and components, so
that ZoneAlarm Pro will check all components against their fingerprints when
a program accesses the Internet.
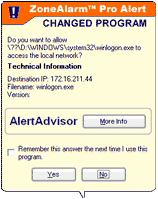
When a program accesses network resources, ZoneAlarm Pro uses the selected authentication method to ensure the that the program hasn't been tampered with. If the program has changed, ZoneAlarm Pro displays a Changed Program alert like the one at left. |
MD5 signature
A digital "fingerprint" used to verify the integrity of a file. If
a file has been changed in any way (for example, if a program has been compromised
by a hacker), its MD5 signature will change as well.