Back tracing enables you to pinpoint the source of data from a logged event. Like retracing a criminalÆs path at a crime scene, back tracing shows the exact steps that incoming traffic has made before reaching your computer and being logged by the Personal Firewall.
The option to back trace a log event is available in both the Security and Traffic logs.
To Backtrace a Log Event
In an open log file, click on an event until it is highlighted.
Right-click on the highlighted event.
A pop-up window prompts you to BackTrace.
Click on the BackTrace option.
The Personal Firewall begins back tracing the event.
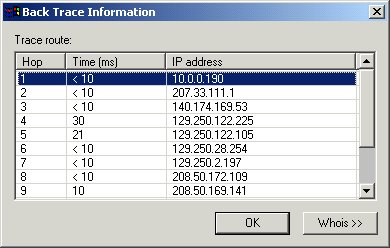
The BackTrace Information window is displayed. Information appears regarding the backtracing of the IP addresses that the log event data visited before arriving at your computerÆs front door.

The Trace Route field provides details on each ôhopö made by the data packet that was logged by the Personal Firewall. A ôhopö is a transition point, usually a router, that a packet of information travels through at as it makes its way from one computer to another on a public network, such as the Internet.
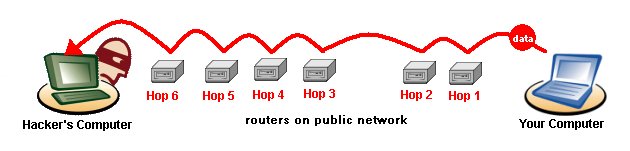
Backtracing is the process of following a data packet backwards, discovering which routers the data took in order to reach your computer. In the case of a Security Log entry, you can trace a data packet used in an attack attempt. Each router that a data packet passes through has an IP address, which is provided in the Trace Route field.
WhoIs
Clicking the WhoIs button prompts the Personal Firewall to pull up detailed information on each hop logged in the Trace Route field. The information is displayed in a drop-down Detail Information panel. Please note that the information displayed does not guarantee that you have discovered who the hacker actually is. The final hop's IP address lists the owner of the router that the hackers connected through, and not necessarily the hackers themselves.

You can cut and paste the information in the Detail information field by pressing Control+C to copy the information to the Windows clipboard, and then pasting it (Control+V) into an e-mail message to your system administrator, for example, asking about a particular site that connects to your computer.
Please note that the information provided in the Detail Information panel should be used responsibly. It is not advisable to contact persons listed in the Detail Information field unless you are experiencing a high number of security logs in which the attacks originate from one particular IP address.