Microsoft Windows Servers run many services and programs. Some of these services need to communicate with other Windows Servers in order to complete their tasks. Sometimes, a Windows server needs to create a "session" with another Windows server. In some cases, a Windows server will login to a remote Windows Server using a blank username and password. This is referred to as a "Null Session".
Unfortunately, a number of hackers have learned that they also can login to some remote Windows Servers using a blank username and password. They can use this to obtain NetBios information from this machine, and to perform various other exploits against this machine. This is referred to as exploiting the "Null Session Vulnerability".
InternetPeriscope allows you determine if your Windows machines are susceptible to the "Null Session Vulnerability".
In order to complete this test on one of your servers, you must run InternetPeriscope on a machine that is not logged in to that server (i.e. not currently sharing a drive or printer, and not logged onto the server's domain, if any.)
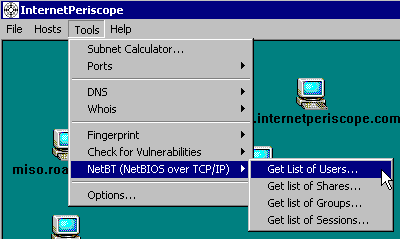
To check for this vulnerability, click on the Tools menu, move your mouse over the "NetBT" menu item, and click on the "Get list of users..." menu item, as shown in the figure.
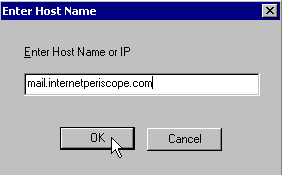
Enter the domain name of your Windows server in the resulting dialog box.
After a few moments, you will see an error message.
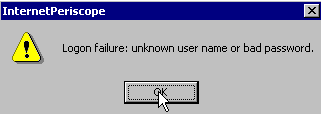
If you do not see an error message, then you are already logged into this remote server. Log out of the server (try rebooting your machine), or run the test from another machine that is not currently connected to the server.
Click on the OK Button, to remove the error message, and you will see the dialog shown below.
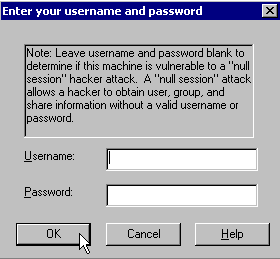
We wish to test for the "Null Session Vulnerability" by attempting to login to the remote host using a blank username and password. Leave the username and password fields blank, and click on the OK button.
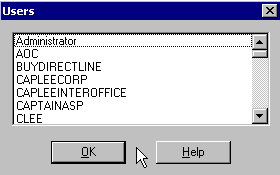
A dialog appears, displaying a list of user accounts on that machine. We were able to see this list of user accounts by using a blank username and password. This tells us that this machine is vulnerable to the "Null Session Vulnerability". Had InternetPeriscope instead presented us with another error message, we would know that this machine is not prone to that vulnerability.