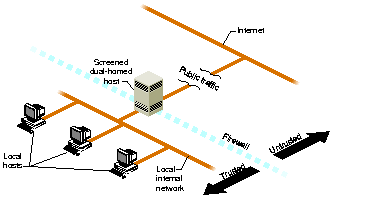
An example of a simple firewall is shown in Figure 5-1. In this illustration, a single computer host is configured with two network interfaces to become what is known as a dual-homed host--a host with a presence on each of two different networks. When it is configured as described in this chapter, it represents a single, controlled obstruction between your internal network and the Internet where you can focus your security efforts. In this chapter, the term firewall host refers to an IRIX host configured for network security. (Gauntlet(TM) for IRIX is an example of a commercial firewall implementation for IRIX--see your sales representative for details.)

Figure 5-1 : A Simple Firewall Environment The firewall does not in any way restrict interactions on your internal network. Local hosts may share resources in the same way they did before connecting to the firewall. What is different now is how these hosts may interact with external sites as determined by your site policy--your policy determines how much or how little interaction is allowed. "Internal Network Configuration" presents some scenarios of how you might configure a network with a dual-homed host.