
SiGnet LR/RR2000 LOCAL/REMOTE ROUTER USER'S GUIDE


"Bridges... More important than houses, more sacred, being more universal, than temples. Everyone's and equal to everyone, useful, always built meaningfully, on places where most human needs meet, more endurable than other edifices, serving no mystery or evil."
Ivo Andri}, Nobel Prize Winner
" Mostovi... Oni su va`niji od ku}a, svetiji, jer op{tiji, od hramova. Sva~iji i prema svakom jednaki, korisni, podignuti uvek smisleno, na mestu na kom se ukr{tava najve}i broj ljudskih potreba, istrajniji su od drugih gradjevina i ne slu`e ni~em {to je tajno ili zlo."
Ivo Andri}
 About SiGnet
About SiGnet INTRODUCTION
INTRODUCTION
 SIGNET IP ROUTER LR/RR2000
SIGNET IP ROUTER LR/RR2000 USING THE SIGNET ROUTER LR/RR2000
USING THE SIGNET ROUTER LR/RR2000 APPENDIX
APPENDIX GLOSSARY
GLOSSARY
 About SiGnet
About SiGnet Through a selection of features that combine high speed, reliability and industry-standard non- proprietary network management, SiGnet products enable corporate-wide access to critical data and ensure the most efficient configuration and distribution of system resources.
SiGnet products comply with industry-standard operating systems and communication protocols, providing users with advanced flexibility and outstanding performance. All SiGnet products are compatible with system software from Silicon Graphics, Hewlett Packard, IBM, Novell, DEC etc., and conform to applicable international communication standards.
Welcome to the SiGnet Ethernet Bridge and Router series which are a part of the SiGnet network prod ucts family. They represent an ultimate achievement in reliable and innovative computer technology.
 INTRODUCTION
INTRODUCTIONBridges have become commonplace in the world of local area networks (LANs) and they have been proven to be an effective internetworking method. With bridges, large networks can be segmented into smaller ones, LANs from different departments can be linked and users of LANs at remote locations can have access to central resources. Bridged networks offer the user corporate-wide access to critical information, improving communication and productivity throughout the organization. Today's bridges provide high performance, comprehensive bridge management and simple installation--all for a relatively low cost.
Using bridges, network administrators can improve network performance, security, reliability and manageability. Bridges used to segment large networks into smaller subnetworks improve performance on each part while still providing transparent access to services for all users. Performance is improved because in a properly planned network most traffic is confined the local segment and there is less traffic on remote network physical media. For example, consider a network of one hundred end-stations and two servers (Figure 1):
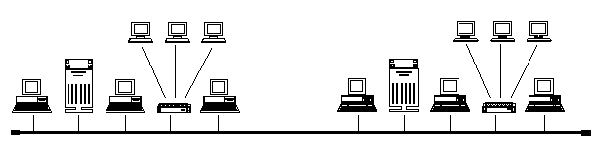
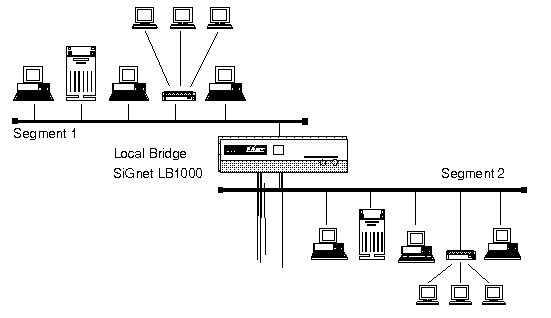
System reliability is increased in many ways. If a section of a segmented LAN fails, other segments are not affected, thus reducing the impact of the failure on users. Alternative links can be automatically activated whenever the main link fails so there is no inteRR2000on of service. Smaller segments also facilitate faster problem isolation.
Repeaters operate at the physical layer of the ISO Reference Model (page 6). They have no intelligence and are used simply to extend the physical cable of the network. They pass all traffic between the segments.
Routers, which are the most intelligent, operate at the Network Layer. They are protocol dependent and connect LANs running the same protocol. Routers are not concerned with the physical layers of the network. Routers trade information between themselves and gain knowledge of the network topology. Based on a variety of parameters, routers choose the best route for packets to travel through the network.
Bridges which, from intelligence point of view, are between repeaters and routers, operate at the Data Link Layer. They have no knowledge on the network topology and are protocol independent. Packets are transfeRR2000forwarded) in the transparent scheme based on destination address and for source routing by the routing information contained in each packet.
Remote bridges overcome distance limitations. Users world-wide can be connected through a wide area network (WAN), no matter where they are located.
A transparent bridge, which operates at the Data Link Layer, works simply by determining whether or not a packet is destined for another station on the same physical ring: If not, the packet is forwarded over the link to connected LANs. Through a process called learning the bridge looks at all packets originating from the physical LAN and creates a table of source addresses. A table is kept for each LAN connected to the bridge. The tables are updated as new packets are encountered and addresses that have not been used for a specified amount of time are deleted.
The bridge looks at the destination of each packet (the process known as filtering) and compares it to the table of source addresses. If a match is found, it means that source and destination addresses reside on the same segment; thus, the packet is ignored by the bridge and is received only by the end- station on the same physical LAN. If a match is not found, the packet is sent over the link to the next physical LAN. Since the bridge has no knowledge of the network topology or where the destination is, it simply passes the packet.
With their ability to go deeper into packet formats, router can provide segmentation, essentially interconnecting separate subnetworks rather than forming one, logically unified network as a bridge does (Figure 3).

As network layer connectors, they are protocol specific. Benefits which offers IP routing are:
TCP/IP networks use 32-bit address to identify a host computer and the network to which the host is attached. The structure of the IP address is IP Address = Network Address + Host Address. IP addresses are classified by their formats. Four formats are permitted: class A, class B, class C and class D.
The class A address provides the networks that have a large number of hosts. The host ID field is 24 bits. Therefore, 224 hosts can be identified. Seven bits are devoted to the network ID, which supports an identification scheme for as many as 127 networks.
Class B addresses are used for networks of intermediate size. Fourteen bits are assigned for the networks ID, and 16 bits are assigned for the host ID. Class C networks contain fewer than 256 hosts. Twenty-one bits are assigned to the network ID. Finally, class D addresses are reserved for multitasting.
The maximal number of network and host addresses that are available for the class A, B, and C addresses are as follows:
Class Maximal network number Maximal host number A 126 16,777,124 B 16,384 65,534 C 2,097,152 256
Formal Internet addresses are issued only to those users that are communicating through the DARPA internet network. These addresses are administrated by the Network Information Center (NIC), which is a part of SRI International.